We know that every hacker use hardware for hacking today we discuss about them......
First:
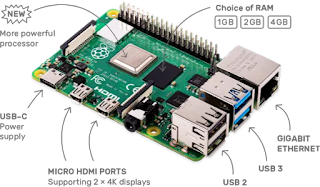
We are now on the third generation of these low-budget computers, which can be used in multiple ways. A classic example in security audits is to use a Raspberry Pi with its appropriate battery pack, a distribution platform like Kali Linux , and applications like FruityWifi, which together act like the Swiss army knife of pentesting.
Is small—tiny in fact
Low cost—around $40
Low power—uses around 2W
Has GPIO (general purpose IO pins)—like the Arduino’s pins, these are used to connect external electronics
Thanks for reading please give me feedback.........
First:
Raspberry Pi 4
Is small—tiny in fact
Low cost—around $40
Low power—uses around 2W
Has GPIO (general purpose IO pins)—like the Arduino’s pins, these are used to connect external electronics
Second:
WiFi Pineapple
This is my favorite tool..................................................................................................
WiFi” Pineapple is a pen testing tool, originally created in order to allow IT professionals to test the vulnerability of their networks. They can be used to de-authenticate and spoof a legitimate network, forcing employees to connect to this fake network.This set of tools for wireless penetration tests is very useful for various types of attacks, such as man-in-the-middle attack
- Dual Band 2.4/5 GHz
533 MHz Network SoC - Four Long Range Antennas
up to 800mW per radio - USB Ethernet, USB Serial,
USB Host and Ethernet Ports - 2 GB NAND Flash
- Power via USB or DC
Alfa Network Board
Every hacker use this for injecting packets. The Alfa stands out for the quality of its materials, and for its use of chipsets which can be set to monitoring mode – a requirement for wireless audits.
Rubber Ducky
This gadget is very useful .Since 2010 the USB Rubber Ducky has been a favorite among hackers, pentesters and IT pros. With its debut, keystroke injection attacks were invented – and since it has captured the imagination with its simple scripting language, formidable hardware, and covert design
HackRF One
this is open source hardware for software-defined radio.
This tool installs a powerful SDR (Software-Defined Radio) system. In other words it is essentially a radio communication device which installs software to be used in place of typically installed hardware.
This is open source hardware for software-defined radio. This way, it is capable of processing all kinds of radio signals ranging from 10 MHz to 6 GHz from a single peripheral, which can be connected to the computer via a USB port.
Proxmark3 Kit
The latest revision of the Proxmark III is the Proxmark3 RDV4 kit that enables sniffing, reading and cloning of RFID (Radio Frequency Identification) tags. It is currently the “gold standard” when it comes to RFID research.
Ubertooth One
The Ubertooth One is an open source Bluetooth test tool from Michael Ossmann.This device is an open-source 2.4 GHz code development platform for experimenting with Bluetooth, enabling users to appreciate the different aspects of new wireless technologies.